Firewall Authentication: Strengthening Network Security in the Digital Age
In an era where cyber threats are growing more complex and damaging, organizations can no longer rely solely on traditional security measures. Firewall authentication has become one of the most critical layers of defense, bridging the gap between access control and user verification. By requiring users or devices to prove their identity before crossing the firewall barrier, this approach ensures that only authorized entities interact with sensitive systems and data. Far beyond simple IP filtering, firewall authentication integrates identity verification, encryption, and policy enforcement, making it a powerful security strategy for businesses, institutions, and even personal networks.
Understanding Firewall Authentication
Firewall authentication refers to the process of validating a user’s or device’s identity before granting access through a network firewall. Traditionally, firewalls functioned like digital gates, blocking or allowing traffic based on predefined rules such as IP addresses, ports, and protocols. While this was effective for many years, the growing sophistication of cyberattacks and the increase in remote work made it clear that more advanced safeguards were necessary.
Instead of simply filtering traffic, firewall authentication adds an additional requirement: proof of who or what is trying to enter. This verification can take many forms—passwords, digital certificates, multifactor authentication, or integration with identity management systems. For example, when an employee logs into a company’s network remotely, the firewall might challenge them for credentials before opening access to internal resources. Only after a successful authentication does the firewall allow traffic to pass, closing the door on many unauthorized attempts.
The beauty of firewall authentication lies in its flexibility. It can secure corporate intranets, cloud applications, public Wi-Fi networks, and even Internet of Things (IoT) environments. By integrating user verification into the very first line of network defense, it significantly reduces the risk of breaches, data theft, and unauthorized use.

How Firewall Authentication Works in Practice
When a user or device attempts to connect to a protected network, firewall authentications begins by intercepting the traffic. Before any data is exchanged, the firewall prompts for verification. Depending on the setup, this may involve entering a username and password, presenting a digital certificate, or using multifactor methods like an OTP or biometric scan.
Behind the scenes, the firewall compares the provided credentials against a trusted source. In smaller setups, this might be the firewall’s internal database. In larger organizations, the firewall connects to external authentication servers, such as RADIUS, LDAP, TACACS+, or Active Directory. These servers validate the credentials and send a response back to the firewall. If the authentication is successful, the firewall updates its rules dynamically, granting access to the appropriate resources based on that user’s identity and permissions.
This process allows for granular control. A marketing employee might be allowed to access email and shared drives but blocked from developer servers. A contractor might be limited to one application for the duration of their engagement. By tying firewall rules to identities rather than just IP addresses, firewall authentication creates a smarter, more adaptable security model.
Types of Firewall Authentication Methods
The strength of firewall authentication comes from its ability to support multiple verification methods, allowing organizations to choose the right level of security for their needs.
- User-Based Authentication: This is the most common form, where users log in with a username and password. Often used in small to medium businesses, it’s straightforward but increasingly paired with additional security measures.
- Device-Based Authentication: Here, the firewall verifies the connecting device rather than (or in addition to) the user. Digital certificates, MAC address filtering, or secure hardware tokens might be used to prove the device’s identity.
- Multi-Factor Authentication (MFA): MFA adds a crucial layer by requiring two or more forms of proof—like a password plus a code sent to a phone, or a fingerprint plus a smart card. This significantly reduces the risk of compromised credentials leading to a breach.
- Application-Level Authentication: Some firewalls require authentication for specific applications or services. This means that even after a user gains network access, they must prove their identity again before reaching sensitive applications.
By mixing and matching these methods, businesses can build a firewall authentication setup that balances convenience and security.
Why Firewall Authentication Matters Today
Cybersecurity is not just an IT issue—it’s a business survival issue. Data breaches cost companies millions, erode trust, and can trigger severe legal consequences. Firewall authentication addresses these challenges by tightening one of the most fundamental control points: the network boundary.
The main benefits of firewall authentication include:
- Stronger Access Control: By ensuring that only verified users and devices can pass, the firewall becomes a true gatekeeper rather than just a passive filter.
- User-Based Policies: Access rules can now follow the user rather than the IP address. This enables dynamic permissions and makes networks far more adaptable to remote work.
- Improved Auditing and Compliance: Every login attempt is logged, creating an audit trail for security teams and for compliance with regulations like GDPR, HIPAA, or ISO standards.
- Defense Against Credential Abuse: MFA and certificate-based approaches mean that even if a password is stolen, attackers can’t easily gain access without the second factor or proper device authentication.
As cyberattacks grow more advanced, these advantages make firewall authentication an essential part of any serious security strategy.

Challenges and Best Practices
While firewall authentication is powerful, it’s not a magic bullet. Organizations must plan and implement it carefully to avoid pitfalls.
Challenges often include:
- Complexity: Setting up and maintaining authentication systems can require expertise, especially in large networks with multiple authentication servers.
- User Experience Issues: Poorly implemented authentication can frustrate users, leading to weaker adoption or risky workarounds.
- Scalability Concerns: As organizations grow, authentication systems must scale without causing delays or bottlenecks.
To overcome these issues, businesses should follow best practices:
- Use MFA whenever possible: A password alone is too easy to compromise; a second factor dramatically boosts security.
- Integrate with central identity systems: Linking the firewall to LDAP, RADIUS, or Active Directory reduces duplication and simplifies management.
- Educate users: Employees should understand why firewall authentication is in place and how to use it correctly.
- Monitor and review logs: Authentication logs can reveal suspicious patterns, such as repeated failed logins or unusual access times.
By addressing these challenges proactively, firewall authentication can be implemented smoothly and effectively.
The Future of Firewall Authentication
Technology never stands still, and firewall authentications is evolving alongside it. Emerging trends will make authentication even more seamless and secure in the coming years.
One trend is passwordless authentication, where users prove their identity with biometrics, hardware keys, or secure tokens instead of passwords. This eliminates the risks of weak or reused passwords entirely.
Another development is context-aware authentication, where the firewall considers factors like the user’s location, device health, and behavior before granting access. For example, if an employee logs in from an unusual country, the system might require extra verification.
Zero Trust Architecture is also reshaping how firewalls operate. In a zero trust model, no user or device is trusted by default—even inside the network. Firewall authentication will play a central role, requiring verification for every request, not just the initial login.
Finally, advances in AI and machine learning may lead to adaptive authentication, where the firewall can adjust security requirements in real time based on perceived risk, streamlining access for trusted users while tightening it for suspicious ones.
🔒 Types of Firewalls
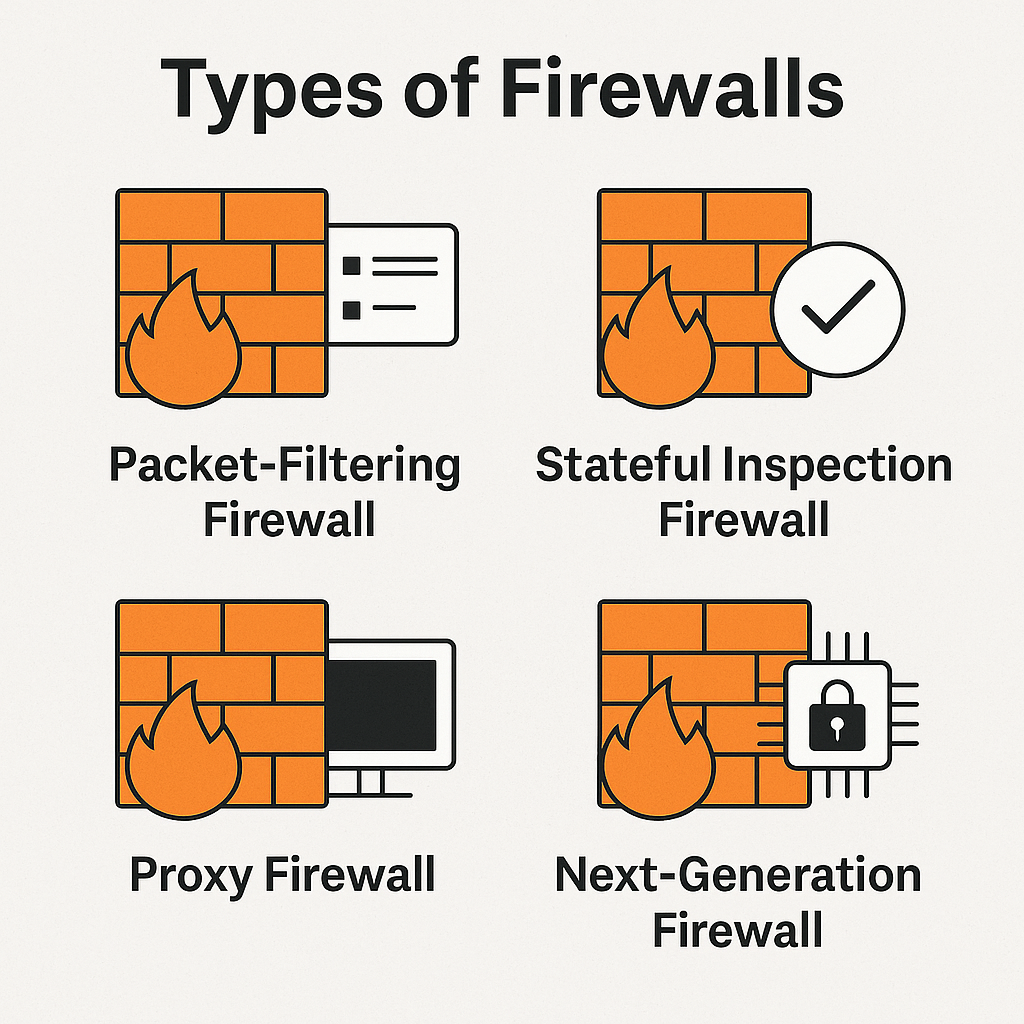
1. Packet-Filtering Firewall
- How it works: Inspects individual packets of data against a set of filters (like IP address, port number, or protocol).
- Pros: Simple, fast, and inexpensive.
- Cons: Doesn’t analyze packet payload (content), so it can miss more advanced threats.
- Best for: Basic network protection.
2. Stateful Inspection Firewall
- How it works: Tracks the state of active connections and makes decisions based on the context of traffic (e.g., is it part of an established session?).
- Pros: More secure than packet filtering; considers the full context.
- Cons: Slower performance compared to stateless filtering.
- Best for: Business networks needing moderate security.
3. Proxy Firewall (Application-Level Gateway)
- How it works: Acts as an intermediary between users and the internet; filters traffic at the application layer.
- Pros: Provides deep packet inspection and anonymity.
- Cons: Can slow down performance and requires more resources.
- Best for: High-security environments (e.g., financial or government sectors).
4. Next-Generation Firewall (NGFW)
- How it works: Combines traditional firewall functions with advanced features like intrusion prevention, deep packet inspection, and application awareness.
- Pros: Comprehensive protection with real-time threat intelligence.
- Cons: Expensive and requires skilled management.
- Best for: Enterprise-level networks and organizations facing modern cyber threats.
5. Circuit-Level Gateway
- How it works: Monitors TCP handshakes and sessions to ensure packets are from legitimate sessions.
- Pros: Efficient and provides some anonymity.
- Cons: Doesn’t inspect packet content.
- Best for: Simple firewall implementations or internal use.
6. Cloud-Based Firewall (Firewall as a Service – FWaaS)
- How it works: Hosted in the cloud; secures cloud infrastructure and traffic between users and applications.
- Pros: Scalable, easier to manage remotely.
- Cons: Dependent on internet connectivity.
- Best for: Businesses using cloud infrastructure or remote workforces.
7. Software Firewall
- How it works: Installed on individual devices to control inbound/outbound traffic.
- Pros: Customizable per device; good for personal use.
- Cons: Doesn’t protect the entire network.
- Best for: Personal computers and small office setups.
8. Hardware Firewall
- How it works: A physical device placed between the network and gateway to block threats.
- Pros: Doesn’t consume system resources; protects the entire network.
- Cons: More expensive than software firewalls.
- Best for: Medium to large businesses.
Why Do Organizations Need Firewalls?
Here are key reasons every organization should implement firewalls:
- 🛑 Block Unauthorized Access: Prevent attackers from accessing internal systems.
- 🔍 Monitor Network Activity: Track what’s happening in real time.
- 🦠 Prevent Malware and Viruses: Stop harmful traffic before it reaches end devices.
- 📉 Reduce Data Breach Risk: First line of defense for sensitive information.
- ✅ Ensure Regulatory Compliance: Many data protection laws require secure network boundaries.
💡 Common Firewall Deployment Scenarios
- Perimeter Security: Firewall at the edge of a network to filter internet traffic.
- Internal Segmentation: Firewalls between departments (e.g., HR and R&D) to prevent lateral attacks.
- Cloud Security: Protecting cloud applications and data from unauthorized access.
- Remote Work Access: Allowing secure VPN tunnels through firewall authentication.
📈 Firewall Trends in 2025 and Beyond
- AI-Driven Threat Detection: Smart firewalls that learn and adapt to traffic patterns.
- Zero Trust Integration: Every request is verified before trust is granted.
- Cloud-Native Firewalls: Designed specifically for multi-cloud and containerized environments.
- Firewall-as-a-Service (FWaaS): Fully managed firewall services, especially for SMEs.
- Policy Automation: Using AI/ML to automatically create or modify firewall rules based on risk profiles.
Real-World Applications
- Corporate Networks – Employees must authenticate before accessing company servers.
- Cloud Services – Firewalls in cloud environments enforce strict identity checks.
- Educational Institutions – Students authenticate to use online learning portals securely.
- Healthcare Systems – Protects sensitive patient data by allowing only verified staff to log in.
Future of Firewall Authentication
With the rise of Zero Trust Security Models, firewall authentication will continue to evolve. Future trends include:
- Biometric-based authentication at the firewall level.
- AI-driven risk scoring to adapt authentication requirements dynamically.
- Tighter integration with Identity and Access Management (IAM) platforms.
- Use of blockchain for secure, tamper-proof authentication records.
✅ In short: Firewall authentication is no longer optional—it is a must-have defense mechanism that ensures only trusted users and devices gain access to sensitive systems. By combining traditional firewalls with strong authentication, businesses can significantly reduce cyber risks.
Conclusion
Firewall authentication has become a cornerstone of modern cybersecurity. By requiring users and devices to prove their identity before entering the network, it transforms the firewall from a static filter into an intelligent, identity-aware guardian. This not only strengthens access control but also supports compliance, improves auditing, and builds trust in an era when digital security is under constant threat.
As organizations adopt new technologies and face increasingly complex cyber risks, firewall authentication will continue to evolve. From MFA to passwordless logins, from integration with identity platforms to AI-powered adaptive models, the concept will grow more sophisticated. But its core purpose will remain the same: protecting networks, data, and people by ensuring that only the right individuals, using the right devices, can cross the firewall boundary.
For businesses, governments, and anyone serious about digital safety, firewall authentication isn’t just a feature—it’s a fundamental strategy for thriving securely in the connected world.